App security is a requirement, not a nice-to-have. Your organization might lose millions of dollars and a lifetime of trust if a single security breach occurs. So, from the minute you start creating your first line of code, make sure security is at the top of your list.
There have been security breaches that have resulted in millions of dollars being stolen while you were busy creating the most user-friendly, inventive, and interesting apps. Considering our current relationship with smartphones and mobile apps, it's clear that a significant portion of our life-critical data is out there in cyberspace, where it may be accessed by a plethora of cyber criminals.
It just takes a single break-in for criminals to learn our names, ages, home addresses, bank account details, and even our exact location within a few meters. Assailants are always on the lookout for highly sensitive information that is sent between enterprise systems.
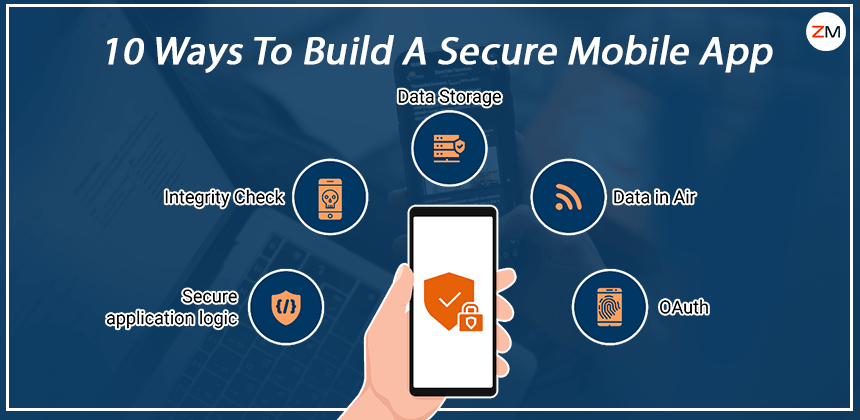
Mobile app developers must do everything they can to protect their customers and users from this kind of danger. Apps can be made more secure in a number of ways, ten of which are listed below:






10 Best Ways to Build a Secure Mobile App

1. Write a Secure Code
The most common method used by attackers to get access to a program is to exploit bugs and vulnerabilities in the code. All they need is a public copy of your software to try to reverse engineer your code and tamper with it. Malicious code affects more than 11.6 million mobile devices at any given moment, according to a study. Harden your code, making it nearly impossible for anyone to break through, from the start. Ensure that your code cannot be reverse engineered by encrypting and compressing it. Repeatedly testing for issues and fixing them as they are found is the best policy. Make it simple to update and patch your code. If a breach occurs, you'll want to keep your code flexible enough that it may be modified by the user. Make your code more secure by hardening it and encrypting it.
2. Encrypt All Data
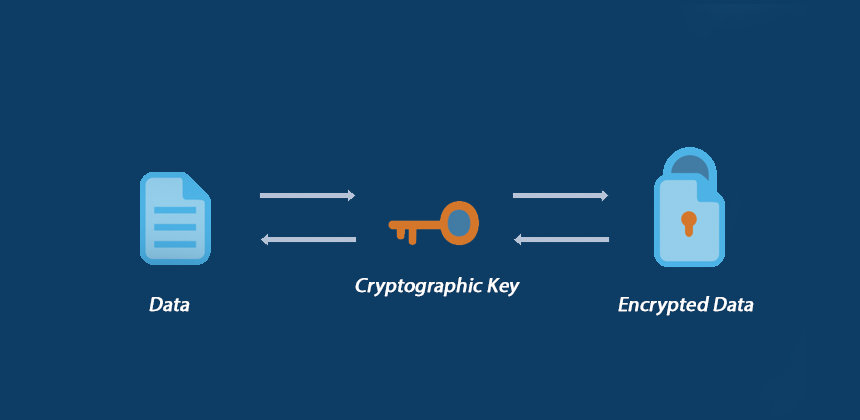
Encryption is required for every bit of data sent through your app's network. Encryption is the process of transforming ordinary text into an alphabet soup that is unintelligible to anybody other than those who possess the secret key. This implies that even if thieves get their hands on the data, they won't be able to do anything with it. When institutions like the FBI and NSA beg for permission to access iPhones and interpret WhatsApp communications, you can grasp the power of encryption. Hackers won't be able to get through if they try to do so on purpose.3. Be Extra Cautious With Libraries
Make sure you properly test any third-party libraries before using them in your project. Some libraries, despite their usefulness, can be exceedingly unsafe for your project. As an example, a weakness in the GNU C Library allowed attackers to remotely execute malicious code and cause a system crash. For seven years, this vulnerability remained unnoticed. Use internal repositories and policy restrictions when acquiring libraries in order to safeguard your apps against library vulnerabilities.
4. Use Authorized APIs Only
Unauthorized and poorly written APIs may unwittingly provide hacker access, which they can then dangerously abuse. For example, programmers can more quickly reuse permission information when performing API calls by caching it locally. It also makes the lives of coders easier by making APIs more accessible. However, it also provides a way for hackers to take control of the system. Using APIs should be done only after they have been approved by a central authority, according to security professionals.
5. Use High-Level Authentication
It's becoming increasingly vital to utilize stronger authentication in light of the fact that some of the biggest security breaches occur as a result of a lack of authentication. Authentication is the use of passwords and other unique identifiers to prevent unauthorized access. It's true that a lot of this is up to your app's end users, but as a developer, you can influence them to be more concerned with things like authentication. As an option, you can set your apps to only accept passwords that must be changed every three or six months. It is becoming more common to use multi-factor authentication, which combines the use of a static password and a dynamic OTP. Fingerprint and retina scanning can also be utilized for biometric authentication in highly sensitive applications.
6. Deploy Tamper-Detection Technologies
In the event that your code is altered or infected with malware, there are ways to notify you. In order to ensure that the code will not work at all if it is modified, an active tamper-detection can be applied.7. Use the Principle of Least Privilege
There should be no more than the permissions necessary for a piece of code, as per the principle of least privilege. No more rights than are absolutely necessary should be requested by your app. Don't ask for access to a user's contacts unless you absolutely require it. Don't connect to unnecessary networks. For a complete list of potential threats, consult your threat modeling tool as you work to improve your app.
8. Deploy Proper Session Handling
Mobile "sessions" last a lot longer than PC sessions. As a result, the server has to work more to manage sessions. A session can be identified using tokens rather than device identifiers. If your device is stolen or misplaced, you can cancel your tokens at any moment. Remotely wipe data from a lost or stolen device, and also remotely log out.
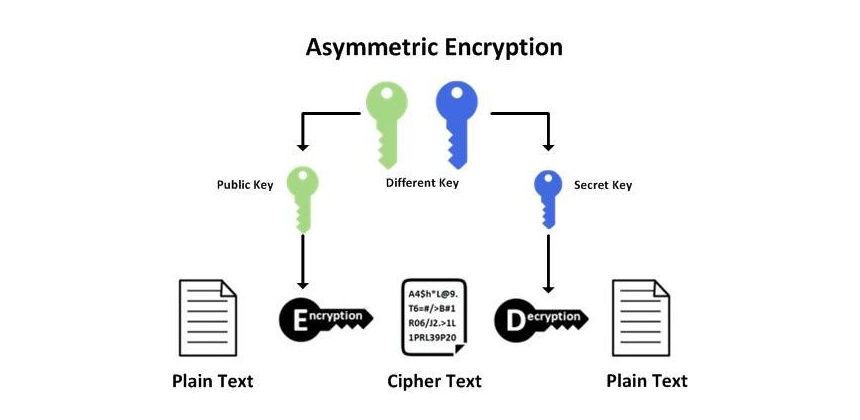
9. Use the Best Cryptography Tools and Techniques
If you want your encryption efforts to succeed, you must handle your keys properly. Do not store your keys in a way that makes them vulnerable to theft if they are hard coded. Keys should never be stored locally on a device, thus keep them in a secure location. Cryptographic protocols such as MD5 and SHA1 have been found to be ineffective by modern standards. 256-bit AES encryption with SHA-256 hashing should be your go-to API.
10. Test Repeatedly
The process of securing your app is never-ending. As new dangers develop, so do the demands for fresh approaches. Keep your apps secure by implementing penetration testing, threat modeling, and emulators. Updates should address these issues, and patches should be released as needed. The WannaCry and NotPetya data breaches of 2017 have surely made everyone realize the importance of cyber security, and the future years will see everyone from corporations to consumers taking it more seriously than ever. Usability and aesthetic appeal will be surpassed by security as a deciding factor in app success.Final Thoughts
Making your software attack-proof can be done in many more ways as well. To be sure, put it into practice. Keeping your app's users and its reputation safe requires ensuring security at each stage of development. You'll maintain your reputation as a mobile app developer if you do this. As a result, your clients and customers will be pleased with your app's security. Choose Zestminds for Secure Mobile App Development For the past 8 years, Zestminds has been a well-known and renowned mobile app development company. Mobile app security is extremely important to us, and we've produced a number of successful iOS, Android, and Windows apps. At every step of the app development process, our developers take the necessary precautions to ensure that the mobile app they create has built-in security protections.

Shivam Sharma
About the Author
With over 13 years of experience in software development, I am the Founder, Director, and CTO of Zestminds, an IT agency specializing in custom software solutions, AI innovation, and digital transformation. I lead a team of skilled engineers, helping businesses streamline processes, optimize performance, and achieve growth through scalable web and mobile applications, AI integration, and automation.
Stay Ahead with Expert Insights & Trends
Explore industry trends, expert analysis, and actionable strategies to drive success in AI, software development, and digital transformation.